Virtual Private Cloud
Virtual Private Cloud (VPC) is a technology that allows you to create your own virtual network within Mammoth Cloud, that isolates your cloud servers on their own private network.
You may define the IP address range and routing table to use for your VPC. These facilities allow the deployment of a wide range of network topologies, determining if (and how) each cloud server has internet access and providing optional VPN connectivity to your corporate network.
Server Management
For customers requiring hands-on assistance in the design and ongoing operation of their VPC environment we have a range of server management options available, from 24/7 monitoring through to full outsourcing.
Virtual Private Cloud Use Cases
Most VPC deployments fall into one of a small number of scenarios. To get started with your own deployment, identify the use case that most closely matches your requirements and provision your VPC to match.
Single-tiered Multi-tiered Multi-tiered + VPN Private-tiered + VPN

1. Single-tiered application
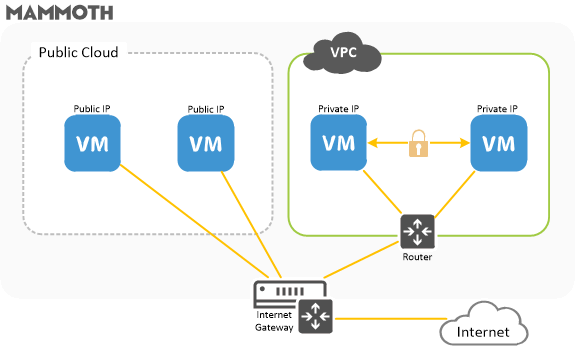
In this use case all cloud servers are deployed into the VPC with their own external IP address, with the router providing access to the internet. We recommend this configuration if you want to run a simple, public-facing web application on a small number of servers.
This scenario consists of:
- A VPC with CIDR block 10.240.0.0/16
- A cloud server with an external IP address (110.232.115.100), which enables internet access
- A virtual router with default routing table
Where multiple servers are deployed in the VPC, the internal IP is used for secure communication between servers.

2. Multi-tiered application
In this use case the application is divided into two or more tiers: an internet-accessible public tier (for example: web servers), and a private tier that is only accessible from within the VPC (for example: database servers). We recommend this configuration for public web applications where you wish to provide additional protection to your backend datastore.
This scenario consists of:
- A VPC with CIDR block 10.240.0.0/16
- A web server with a private IP address (10.240.0.4) and an external IP address (110.232.115.100) forwarded by the router, which enables internet access
- A database server with a private IP address (10.240.0.5) and no external IP address; this server is only accessible from within the VPC
- To provide outgoing internet access to the database server, the route table is configured to pass internet traffic (0.0.0.0/0) to the web server
The web server is configured to provide NAT for the database server, or in a larger deployment a dedicated NAT server may be used.

3. Multi-tiered application with VPN
This use case extends multi-tiered application by adding a VPN connection to your company network. The backend tier is directly accessible from your own network, and may optionally connect to your inhouse servers. We recommend this configuration for migrating your existing web applications into the cloud.
This scenario consists of:
- A VPC with CIDR block 10.240.0.0/16
- A web server with a private IP address (10.240.0.4) and an external IP address (110.232.115.100)
- A database server with a private IP address (10.240.0.6) and no external IP address
- A VPN server with a private IP address (10.240.0.5) and an external IP address (110.232.115.101) which will be the remote VPN endpoint
- Your own VPN gateway which will be the local VPN endpoint, providing access for your company network (192.168.1.0/24)
- The route table is configured to send outgoing internet traffic (0.0.0.0/0) via the web server and to send your company network traffic (192.168.1.0/24) via the VPN server
The web server is configured to provide NAT for the database server, or in a larger deployment a dedicated NAT server may be used.

4. Private application with VPN
This use case provides a private network only accessible via a VPN connection to your company network. The servers are not internet accessible and outgoing internet access is provided by your company network. We recommend this configuration for migrating your in-house applications into the cloud.
This scenario consists of:
- A VPC with CIDR block 10.240.0.0/16
- A cloud server with a private IP address (10.240.0.6) and no external IP address
- A VPN server with a private IP address (10.240.0.5) and an external IP address (110.232.115.101) which will be the remote VPN endpoint
- Your own VPN gateway which will be the local VPN endpoint, providing access for your company network (192.168.1.0/24)
- The route table is configured to send all traffic (0.0.0.0/0) to your company network via the VPN server
The private server has no outgoing internet access other than via your company network. This allows you to provide internet access using the security controls already in place for your existing in-house deployment.

Like to speak
to a hosting expert?
Then speak to this guy, he brings his own cables to work.

Get more from your server